As an "account book that cannot be relied upon", how can the blockchain ensure information security?
When talking about blockchain, its security is often an unavoidable topic. Today, let’s take a look at the secret.
Before discussing its information security mechanism, let’s think about it first. What is the basis of a good transaction?
Trust, yes. From buying breakfast to cross-border remittance and settlement between groups, communication and trust between trading parties are very important. Just as we attach great importance to the reputation and after-sales ability of the platform when shopping online, international transactions also rely heavily on third-party institutions that can provide credit endorsement and communication mechanisms, such as SWIFT organizations.

A good trading foundation is endorsed by trust | |Pixabay
Swift (Society for Worldwide Interbank Financial Telecommunication) is a non-profit cooperative organization among international banks. SWIFT has established a set of identity information standards for financial institutions in different countries, which is called SWIFT CODE. Then, based on the identity information of the same standard, a communication channel with good reputation was established. In international transactions, this trustworthy third-party organization can effectively reduce the cost of mutual trust and verification in the process of information exchange and promote the completion of transactions.
However, with the development of information technology and the oscillation of global political situation, the disadvantages of relying on third-party institutions have gradually become prominent. For example, in 2018, in order to hinder Iran’s international business, the United States cut off SWIFT’s services to Iranian banks.
Although SWIFT is a non-profit international organization in essence, it does not have "nationality", but SWIFT’s online service needs offline equipment to support it, and offline locations have "nationality". In other words, the server is located in the territory of which political entity, and the related operations have to be under the jurisdiction of this political entity. Yes, one of SWIFT’s main servers is located in the United States.
From here, we can see that third-party guarantee institutions are often bound to centralized data storage and processing.
That is to say, technically, the center administrator with the highest authority can modify the data exchange rules of the participants (blocking accounts, reducing authority, etc.); Legally, the operating entities located in a certain territory must also cooperate with the investigation or requirements of the regime.
Therefore, more and more countries and regions are beginning to realize that the centralized system is not a fair balance, and third-party institutions may become "undercover".
To this end, various countries and regions began to set up their own trading systems. For example, Europe introduced the Single Euro Payment Area System (SEPA), and China created the RMB Cross-border Payment System (CIPS) to deal with the potential risks similar to those faced by Iran.
However, if each participant insists on using his own system, it is equivalent to returning to the trading era of "doing things separately", and the problems of credit and communication will resurface.
Let’s re-examine the essence of this dilemma. Centralization, yes, for the economic field, centralization is equivalent to "centralization", which may bring monopoly and uncontrollable risks. Therefore, the fundamental solution to this problem lies not in who has the power, but in decentralization, that is, decentralization.
Blockchain is such an information technology that can support decentralized transactions. Under the premise of decentralization, how to ensure information security has become the main difficulty that blockchain needs to face.
Blockchain uses distributed network and distributed account book technology in data transmission and storage.
What is a distributed network? Simply put, it is to turn your computer into a micro server that can be uploaded or downloaded. Does it look familiar? Yes, Thunder downloaded from BT seeds uses this technology.
In the centralized information network, the central server is equivalent to the commander-in-chief, so once the commander-in-chief is captured, the rest of the military forces will be defeated without a fight. However, the distributed network has no commander in chief in the traditional sense, and computers can communicate directly without the central server. Information will be recorded and stored by all participants, and all participants will collectively maintain and share the platform.
So what is a distributed ledger? Roughly speaking, you can understand the distributed ledger as a "communication soldier" in the blockchain. When any participant updates the data, this operation information will be broadcast to the blockchain, and then the receiver will automatically proofread according to the consensus mechanism of this chain to judge whether the received data is consistent with the locally stored data. When the data is inconsistent, the node will not accept this piece of data update. When the data are consistent, the node accepts the update and saves it. When most participants in the blockchain accept the newly added data through this process, the overall update of the chain is completed.
However, if everyone can update all the data synchronously, doesn’t it mean that everyone can also get each other’s private information?
Actually, it is not. Blockchain adopts an encryption mechanism called "hash function" to solve the security of information preservation. After the data packet is processed by hash function, it will become a line of garbled codes, which can only be verified during transmission and cannot be restored to the original information. The corresponding relationship between the hash function and the real information is saved by the corresponding participants. Blockchain solves the security of data privacy through this way of "treasure box for you, but the key is in my hand".
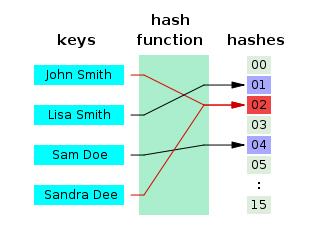
In order to solve the security of information storage, blockchain adopts an encryption mechanism called "hash function" | |public domain.
However, blockchain, like all technologies, is not perfect, but it is more solid than existing similar technologies. For example, when Zhang San tries to influence Li Si by tampering with information, Zhang San can’t directly attack Li Si, but needs to calculate the values of all hash functions contained in the block structure, which requires a lot of calculation and computing power that ordinary participants can’t achieve, that is, the threshold of tampering is extremely high. If Zhang San wants to influence the whole blockchain, it is not enough to influence one, at least it needs to tamper with more than half of the user data in the blockchain. Therefore, compared with the brutal attack mode that the centralized system can "go straight to Huanglong", the tampering of blockchain can be described as "all hands are tied."
In addition, the blockchain also adopts the mechanism of "only increasing but not decreasing", and only supports additive data operations, but not subtractive data operations. This mechanism means that all historical information and operations can be backtracked and proofread. Once malicious operations are found, you can touch the melon along the vine, and there is no "destroying the corpse".
To some extent, in a blockchain, the more participants, the more stable the system. Every information transmission is equivalent to having the credit endorsement of all participants in the blockchain.
In the turbulent era, the concept of "I am for everyone and everyone is for me" contained in the blockchain may be the best way to break prejudice and build a system of mutual trust and stability.
references
[1] Coron J S , Dodis Y , Malinaud C , et al. Merkle-Damgrd Revisited: How to Construct a Hash Function[C]// International Cryptology Conference. Springer Berlin Heidelberg, 2005.
[2] Christidis K , Devetsikiotis M . Blockchains and Smart Contracts for the Internet of Things[J]. IEEE Access, 2016, 4:2292-2303.
[3] Marc P . Blockchain Technology: Principles and Applications[J]. Post-Print, 2016.
[4] Yuan Yong, Fei-Yue Wang. Development Status and Prospect of Blockchain Technology [J]. Zidonghua Xuebao/Acta Automatica Sinica, 2016,42 (4): 481-494.
[5] Iansiti M , Lakhani K R . The Truth About Blockchain:[J]. Harvard business review, 2017, 95(1):118-127.
[6] He Pu, Yu Ge, Zhang Yanfeng, et al. Overview of blockchain technology and application [J]. Computer Science, 2017, 44(4):8.
Author: Wang Yuhao
Editor: Han Yueyang

Source: Guangming Net